With growing government regulations around the world and concerns about insider threats and other vulnerabilities, the need to encrypt data at rest (DAR) has never been greater. Medical records in the U.S., Canada, Europe and parts of Asia are a good example of data types that require DAR encryption.
There are two methods for DAR encryption. One uses the CPU to write all data to the specified encryption algorithm, and the second uses the storage device to encrypt the data. We will examine the advantages and costs of each method.
If you use DAR encryption, and the storage device is removed from the environment, it will be useless to someone outside of the physical environment. And in many cases it will be useless even within the same enclosure in a different position. You cannot just move encrypted disks or SSDs around because the device is often keyed to the enclosure. File-level encryption is also supported by hardware instructions on ARM, IBM and Intel CPUs and provides encryption from the server to the device.
Background On Both Encryption Methods
File-level encryption uses the CPU on the host to encrypt the data. Intel CPUs have a set of hardware instructions that take an encryption key and encrypt the data using the AES encryption algorithm, with key sizes of 128 bits or 256 bits. Obviously, 256 bit keys are more secure than 128 bit keys.
Device encryption for most disk drives and SSDs from most vendors uses the same AES algorithm and key sizes, but instead of being an instruction in a CPU, it is part of the hardware design and runs at the full rate of the device with no degradation of the data rate to the disk or SSD devices.
Performance Numbers
Most disk vendors and SSD vendors run a full data rate, but if DAR encryption is required, it is important to ask about performance before making a purchase to ensure that a device runs a specified rate with encryption.
I have not found a lot of performance data on host-based encryption. The Intel CPU instructions show a rate based on the CPU type, and scaling is done by adding additional CPUs. A paper written a few years ago shows the performance at that time, and it is likely a good assumption that that performance has scaled with the CPU performance. Here is some key verbiage from the white paper:
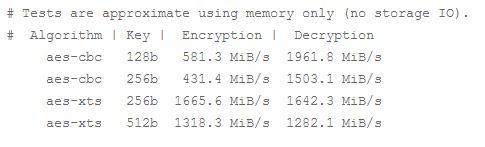
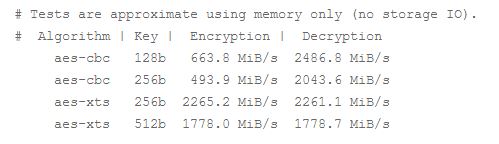
On Ivy Bridge here are the raw numbers for both Cyber-Block-Chaining (CBC) and XEX-based tweaked-codebook mode with ciphertext stealing (XTS) modes with both 128- and 256-bit keys. Note that for XTS mode, only half the key is used, so XTS-512 essentially utilizes a 256-bit key.
# Tests are approximate using memory only (no storage IO).
And for Haswell:
Performance clearly improves with newer CPUs, and it is likely that the latest CPUs improve upon the above performance. Just taking the Haswell CPU example, it does not take more than 10 disk drives or two SSDs to saturate performance and require additional CPUs, assuming the storage devices run at the expected device rates, and most do.
Encryption Costs
If a system requires DAR encryption and is used to ingest large amounts of data, as is the case for the medical industry, streaming video capture from security cameras, or any other workflow with large data ingest, DAR encryption is best architected using the encryption that comes with every disk or SSD. There is no extra cost for extra CPUs to support encryption at the file level, as disks and SSDs have encryption built into the controller ASIC for all Seagate enterprise storage. With device encryption, the performance scales with the number of devices, unlike CPU-based encryption, which requires additional CPUs to support encryption for every two SSDs or ten disk drives.
The Advantage Of Device Encryption
If your security requirements include DAR encryption, then using the native encryption capability on the disk or SSD device is both higher efficiency and lower cost. Additionally, if a disk or SSD is failing and it needs to be removed or you are upgrading, simply removing the key on the disk or SSD device makes the device unusable in another storage system.
With far more scalable performance and no additional cost for the devices in both power and capital costs, DAR encryption is best done on the disk and SSD devices rather than on CPUs.